Because Security Gives Us Freedom.
The Panoptic Approach
Security is a process, not a product.
Data Mirrors Policy
The onShore Security Process ensures that data mirrors policy. Our Panoptic Cyberdefense™ Security Operations Center (SOC) Service is a cybersecurity professional service involving high-level consulting, monitoring, data collection, analysis, security management, and reporting. We typically serve regulated industries and enterprises with complex networks and the need for 24hr cybersecurity response. We integrate with your IT organization to increase security visibility, provide reporting for management and regulators, and inform policy.
24-Hour Staff
We manage, monitor, analyze, alert, and dispatch 24 hours a day, 7 days a week.
Attacks are now often multi-vector, multiple exploit, with 55% of them beginning with social engineering. Our approach is holistic. In a post-Sony era, we assume every network is vulnerable inside and outside. Customer policy informs rules and tuning - what is best for one company may not be acceptable for another. During our two month onboarding process, we heavily tune our sensors to establish a baseline of your network with hundreds of parameters matched against characteristics of your policies, risk appetite, and regulatory compliance.
Correlation Across All Points
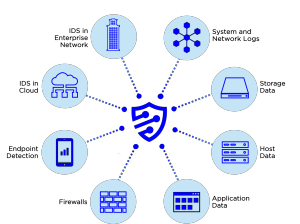
We collect data from any system, our sensors on your site, cloud-placed sensors, netflow collectors, firewalls, and network devices, including encrypted payloads, and correlate that with logs from your systems to achieve an end-to-end security view. Security engineers analyze correlated data daily, augmenting and continuously tuning your customized signatures against industry sources and our own 15 year database.
Our reporting provides fully navigable SIEM data, as well as C-level status briefs and threat landscape reviews, currently making up 12 standard recurring reports and additional custom reports on request. All firewalls and sensors are managed with off-site logging, configuration management, and change control to your policies. We provide our audited SOC2 control matrix at your request.
IDS in Cloud
VM IDS collectors watch traffic to your applications.
IDS in Enterprise Network
Core-switch span ports provide visibility, even into encrypted payloads.
System and Network Logs
Protection, deception, NAC, and other network-based sources provide powerful correlation data.
Firewalls
Activity on both sides reveal the nature of an attack. Advanced protection feature logs are ingested for alerting and analysis.
Storage Data
Monitor for compliance to access policies.
Host Data
AD and host agent logs correlate against network activity and alert on anomalous behavior.
Application Data
Application access and baseline behavior set alert thresholds.
Endpoint Detection
Endpoint detection agents provide visibility into the most vulnerable attack surface through behavioral analytics, application whitelisting, and microsegmentation.