Because Security Gives Us Freedom.
Managed Detection and Response (MDR)
Panoptic Cyberdefense® Goal: mitigate risk, protect sensitive data, provide visibility to upper management, elevate your security team, all while satisfying compliance requirements.
True threats (high value alerts) need to be separated from your network’s high volume of benign activity, and require immediate attention. Managed Detection and Response, as part of our Panoptic Cyberdefense® managed service, offers this peace of mind without the cost or hassle of operating a Security Incident & Event Manager (SIEM).
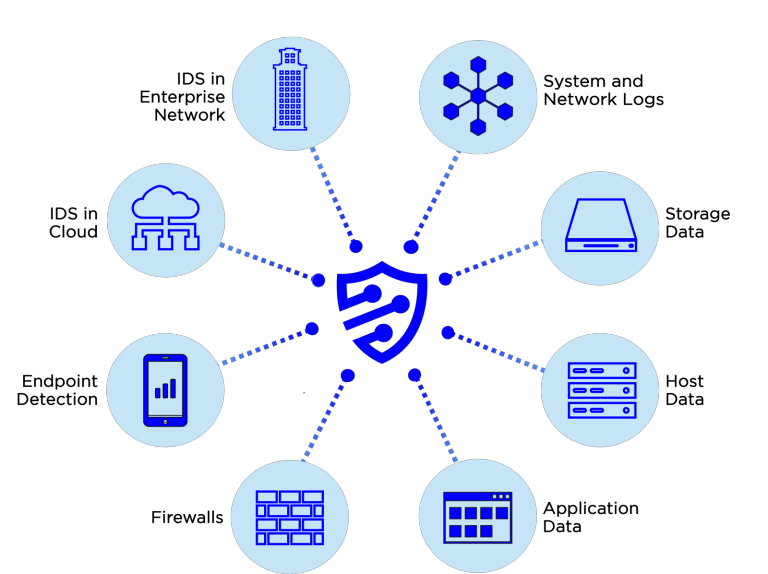
Accepting security data from all systems in your network into our ELK Stack-based Panoptic SIEM® we will monitor, correlate, and alert on threats, anomalies, and compliance violations 24/7.
Our SIEM and alerting systems are in our private cloud. We place our Panoptic Sensor® on your site or in any virtual environment. In concert with our Panoptic Approach, our SIEM accepts almost any output from Active Directory, firewalls, intrusion detection systems (IDS), data loss prevention (DLP) systems, endpoint detection, and many others.
How MDR Works

Security Event & Log Correlation
Correlation of security data is the heart of security management. But we go beyond that with rule customization and data tools that empower the analyst to detect threats, anomalies, and compliance violations.

Panoptic SIEM®
Receive only truly actionable information and alerts. Our ELK Stack-based Panoptic SIEM® uses the most advanced machine-learning analytics available.
24/7 Threat-Level Alerting
Detect on-premise, in the cloud, on virtual workloads, even SaaS applications. Our SOC will alert via ticket, API, email, or phone based on custom, agreed-upon criteria.
Analyze Log, End-point, SNMP, API Data
We'll customize to accept most any log source. Of course we're ready for your AD, firewalls, IDS, DLP, end-point detection and more. Unlike the others, we also analyze switches (SNMP) for parameters not found in logs. Upgrade to MDR+NDR to add full packet captures.
SIEM, Log, & Incident Retention
We retain all SIEM, log, session, and ticket data for 6-months for forensics and analysis. Optional optical disk archives are available for long-term archiving. Upgrade to MDR+NDR for 12-month retention.
Proprietary Signature Updates
We leverage our, proprietary, 17-years collected signature database along with our banking signatures and other commercial and community signature databases, updated continuously and customized for your network.

SOC2 Type II Audited
Security is a process not a product. This is why we track everything in our ticketing system (or yours) and annually perform a SOC2 Type II audit of our operations.
SIEM Reports
SIEM reports aggregate the alerts and correlated security data and deliver it to you in an easily understood format with summaries, trending, and visualization that highlight the nature of your network activity. Reports can be prepared daily, weekly, monthly, or yearly.
Firewall Reports
Firewall reports need special attention. Nexgen firewalls provide more data via API that isn't present in logs. We provide daily and monthly reporting for blocked and filtered content, threat detection, geo-activity, and bandwidth graphing.