Because Security Gives Us Freedom.
Continuous Vulnerability Management
Vulnerability Management is an absolute must for any organization. onShore Security offers a complete, turnkey service, delivered from our private cloud. Have our Elite Blue Team manage this important process for you. The ROI is significant and immediate.
-
Get compliant
-
Heighten security
-
Increase organizational maturity
-
Reduce workload on Infosec teams
-
Provide greater clarity to leadership
 With fully authenticated internal, external, cloud, agent, and agentless continuous scanning we don’t skip an asset on your network, your users, or in the cloud. We provide an always up-to-date image of your overall security risk and threat intelligence that allows us to predict exploitable vulnerabilities. Stand-alone or fully Panoptic Cyberdefense® integrated options are available.
With fully authenticated internal, external, cloud, agent, and agentless continuous scanning we don’t skip an asset on your network, your users, or in the cloud. We provide an always up-to-date image of your overall security risk and threat intelligence that allows us to predict exploitable vulnerabilities. Stand-alone or fully Panoptic Cyberdefense® integrated options are available.
| Key Features | ||
|---|---|---|
| Continuous Scanning | User Behavior Tracking | Network Device and Firewall Configuration Ingestion |
| Customer Portal | Application Vulnerability Tracking | Active Directory Policies |
| Weekly Dashboard Reports | Office 365 Assets and Secure Score | Password Policies |
| Monthly Reporting and Review | Intune Assets Discovery and Tracking | User Analysis |
| External & Internal Network Scans | Azure Assets Discovery and Tracking | Device Analysis |
| Cloud Workload Scans | Asset Vulnerabilities by OS | Per Asset and Company Risk Scores |
| Remote Workstation Scans | Active Directory Users and Groups Compliance | MITRE CVE Mapping |
| Deep Asset Discovery and Tracking | Software Inventory | Elasticsearch and Panoptic SIEM® Integration |
| New Asset Discovery and Tracking | Software Blacklist Report | JSON, XML, CSV Export |
Why Continuous?
 Annual or monthly scans are no longer adequate. There are hundreds of new vulnerabilities added to the MITRE CVE database daily. That means every day that you don’t scan, you don’t know if you’re newly vulnerable. Continuous scanning is the the only answer.
Annual or monthly scans are no longer adequate. There are hundreds of new vulnerabilities added to the MITRE CVE database daily. That means every day that you don’t scan, you don’t know if you’re newly vulnerable. Continuous scanning is the the only answer.
Not Just Scanning
Vulnerability scanning alone isn’t enough. Vulnerability Management takes it up a whole level of maturity by adding expansive vulnerability tracking over time. Now you have patch velocity and performance. You also get analysis by user, OS, and application. Let’s not forget an effective asset audit which is the number one control on most security frameworks. This is the oversight all IT and Infosec teams need without adding to their workload.
![]() Our service instantly and efficiently raises the operational maturity of our clients’ vulnerability management programs. In addition to traditional vulnerability scans, we perform credentialed scans to detect configuration problems that may also cause security vulnerabilities, and deeper, more accurate scanning results overall with wider scan coverage.
Our service instantly and efficiently raises the operational maturity of our clients’ vulnerability management programs. In addition to traditional vulnerability scans, we perform credentialed scans to detect configuration problems that may also cause security vulnerabilities, and deeper, more accurate scanning results overall with wider scan coverage.
All this with our Security Analysts by your side, responding to requests, analyzing reports, and meeting with you monthly.
CVM Benefits
![]()
Compliance
Today all security frameworks, regulations, and insurance require regular vulnerability scanning of your network and workloads. Soon they will require a full vulnerability management program with continuous scanning.
 Security
Security
You can't protect your assets unless you know them. Nor can you mitigate your vulnerabilities unless you know them.
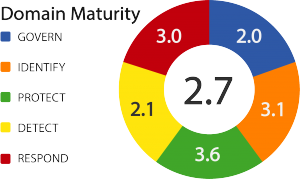 Maturity
Maturity
Your security program gains maturity with clear documentation of your vulnerabilities and metrics of your mitigation efforts.
CVM Process
24/7 Management
• Moves, adds, changes to configuration, repository, scanning agents, and roles/privileges
• Provide scanning system maintenance upgrades, patches
24/7 Monitoring
• Missing patches
• New assets on your network
• Configuration mistakes
• Appliances, agents, compliance dashboards, and scheduled tasks
Analysis