Because Security Gives Us Freedom.
Microsegmentation as a Service
Network Protection and Detection through Endpoint Control
Microsegmentation is deployed to ensure that sensitive systems and information are only visible to the users who need them, as determined by the security policy. This philosophy of security is in line with the “zero-trust model”, with policy written to protect your network down to the application level. Microsegmentation of the network prevents infections and breaches from spreading, effectively isolating compromised workstations and containing malicious activity. This strategy also limits access between VM instances, to enforce segmentation between cloud workloads and user endpoints, regardless of the current configuration of the physical network architecture.
Prevention isn’t enough.
Every organization knows they need to secure their network perimeter to withstand constant assault and prevent intrusion. There’s no perimeter anymore. When every endpoint is a vector, containment is critical. Threats from within the network, however, put your sensitive data and systems at great peril. This is why microsegmentation is an essential part of any security strategy, limiting access between VM instances as well as enforcing segmentation between cloud workloads, non-cloud resources, and user endpoints, independent of network architecture.
OPAQ’s microsegmentation capability, Endpoint Control, allows organizations to take a detailed, granular approach to establishing unique security policies, applied to data center applications, all the way down to the workload and user level.
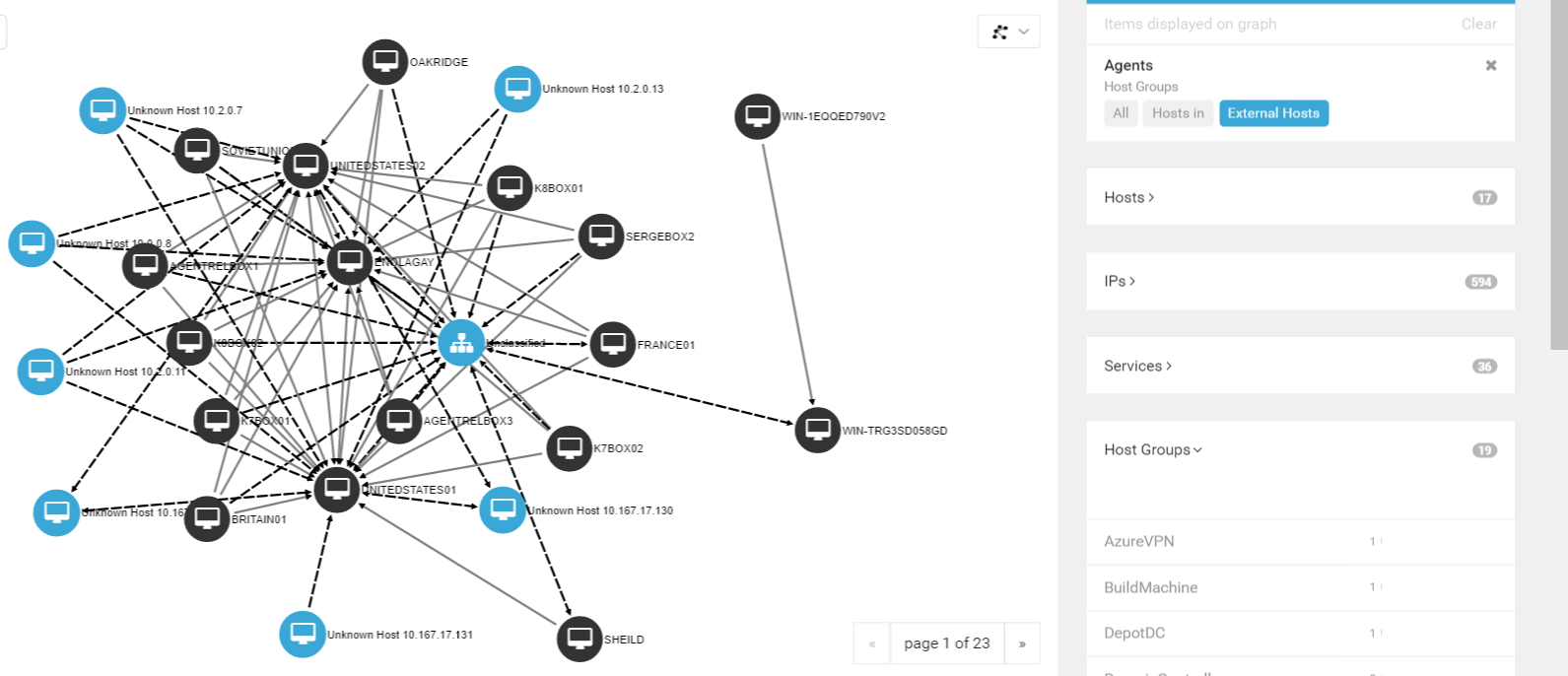
This is Microsegmentation, Simplified
Ransomware is ranked as one of the most prevalent threats on the cybersecurity landscape today. Worms and other automated attacks have been on the rise, spreading from the point of breach across the whole domain. Experts predict the situation will grow worse as  hackers develop their attack automation. The clear answer to the threat is to improve network segmentation, but that is easier said than done.
hackers develop their attack automation. The clear answer to the threat is to improve network segmentation, but that is easier said than done.
Traditional methods of network segmentation, such as implementing internal firewalls and VLANS require time and commitment. Often, network architecture, typically optimized for connection, must be completely re-designed into complex, security minded configurations. The seemingly simple multi-factor authentication can be an intense project, requiring special attention for each application on the network. Using OPAQ cloud solutions, microsegmentation is simplified.
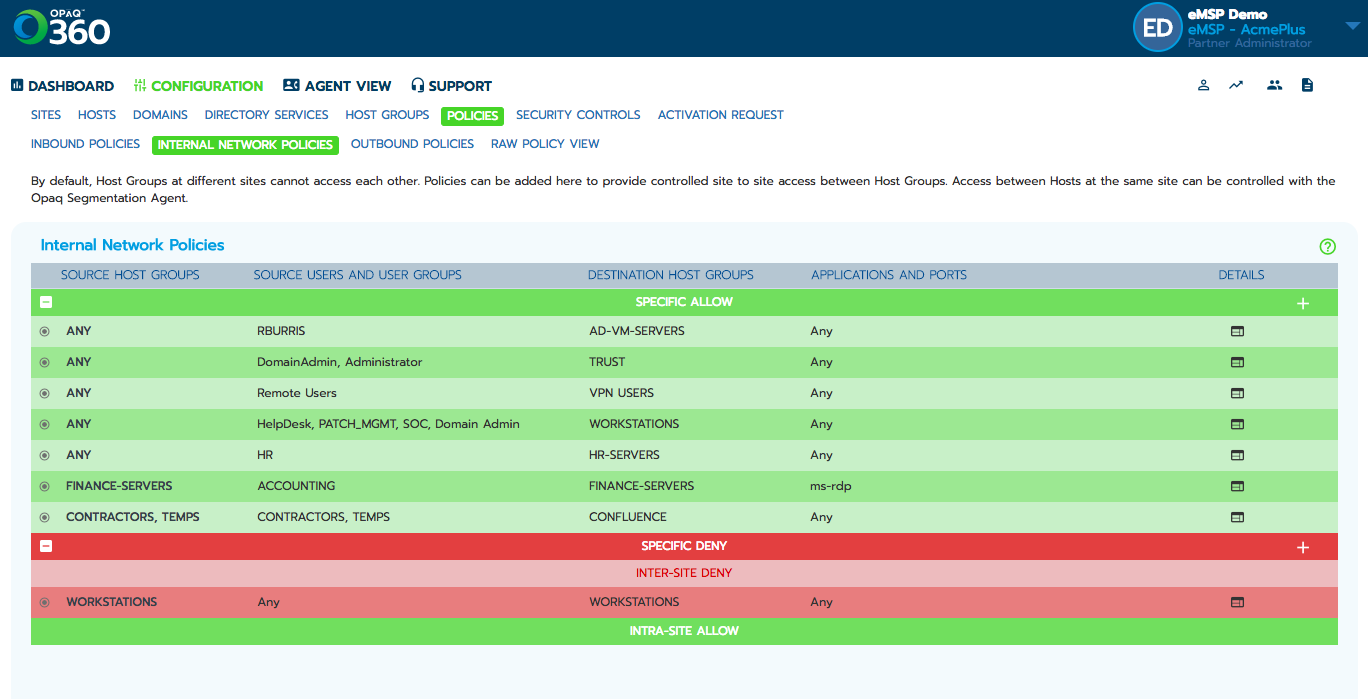
Powered by OPAQ
OPAQ Endpoint Control provides:
• Simple policy logic for stopping users from talking to each other over ports commonly used for malicious propagation. (They shouldn’t be talking on these anyway.)
• Network topology and analytic views that show who’s talking to who and what network processes are running on which endpoint.
• Greater visibility into lateral east-west traffic for optimum network performance and incident response time.
• Easier network segmentation / microsegmentation, which empowers you to structure traffic smartly to protect key enterprise assets from impact.
• The ability to apply Zero Trust security best practices.
• Advanced endpoint security in hours / days versus months, managed through a single cloud console
Features include:
• Host asset inventory
• Host group and user group based software-defined network segmentation, aka microsegmentation
• Instantaneous host quarantine
• Endpoint analysis console
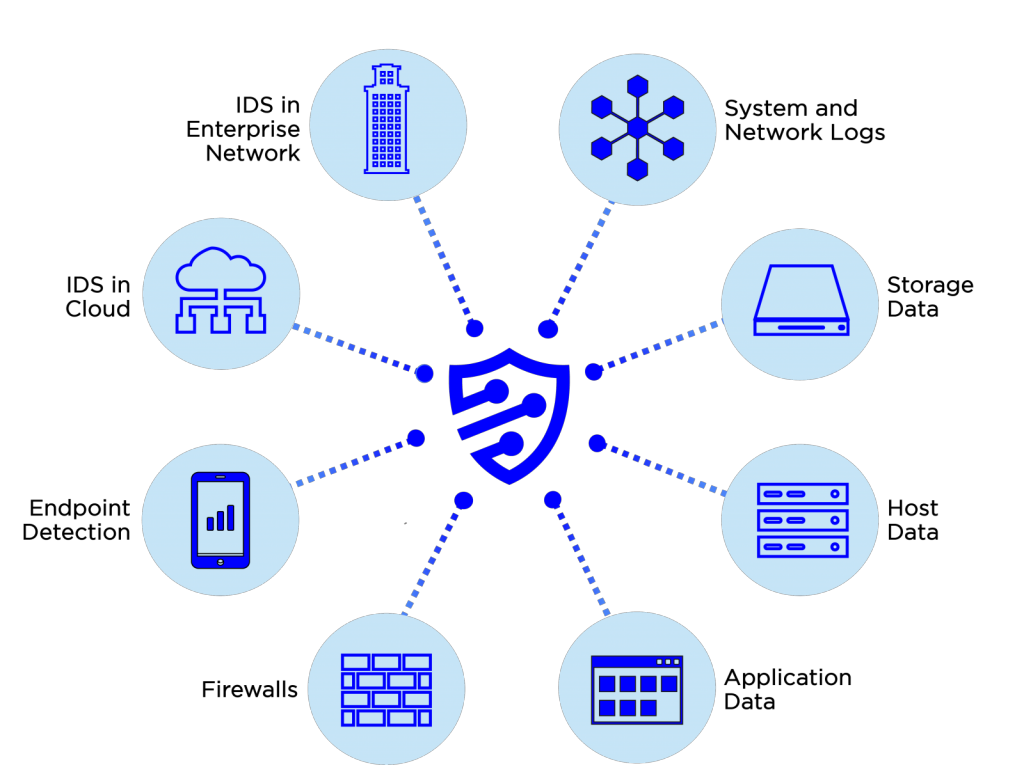
onShore provides microsegmentation as a service and integrates it with our Panoptic Cyberdefense℠ offering.
onShore's Panoptic Cyberdefense℠ service collects data from any system, our sensors on your site, cloud-placed sensors, netflow collectors, firewalls, and network devices, including encrypted payloads, and correlates all data with logs from your systems to achieve an end-to-end security view. Security engineers analyze correlated data daily, augmenting and continuously tuning your customized signatures against industry sources and our own 15 year database.
