Spectre and Meltdown are a pair of newly discovered cyber attacks that “exploit critical vulnerabilities in modern processors”. These programs, which can attack PCs, mobile devices, and even cloud-based machines, seek sensitive data in the memory of other running programs. In particular, Meltdown penetrates the barrier between user applications and the operating system, allowing a program (the exploit, in this case) to access the memory of other programs, including the OS. Software patches against Meltdown and Spectre have been developed, but are reported to be buggy and could potentially cause problems.
onShore Security’s Product Manager, Ryan Thoryk, ran a proof-of-concept to test the vulnerability of his systems. Ryan explains,
“With this utility, the data only shows up if it’s in cache. It looks for the Linux kernel banner, since it’s an easy target and gets cached automatically.The utility first looks up the memory address of the function linux_proc_banner from the file /proc/kallsyms, and then dumps that memory. If the system is vulnerable, the raw kernel version string (that /proc/version uses) will appear and the utility will report “vulnerable”. This basically means that the speculative execution leaves traces of data behind, so the kernel and running programs could potentially have their memory appear and be accessible. Normally, the system would return an error if invalid memory is accessed. However, according to the Wikipedia page on this vulnerability, any kernel memory and memory from other processes can be accessed if exploited, due to the unauthorized memory being loaded into the CPU’s cache during speculative execution. Since many operating systems map physical memory, kernel processes, and other running user space processes into the address space of every process, Meltdown effectively makes it possible for a rogue process to read any physical, kernel or other processes’ mapped memory—regardless of whether it should be able to do so.”
Thoryk says that on cloud-based systems, virtual machines cannot access another virtual machine’s data, but the host machine can still access each virtual machine’s data.
For Thoryk’s proof of concept, he ran a series of five demos (available on GitHub). The first demo “uses Meltdown to read accessible addresses from the own address space, not breaking any isolation means.” The second demo attempted, successfully, to “break” the Kernel Address Space Layout Randomization in Linux. By default, the location of the kernel (and the direct physical map of the memory) changes with each reboot. This second demo uses Meltdown to leak this randomization of the physical map.
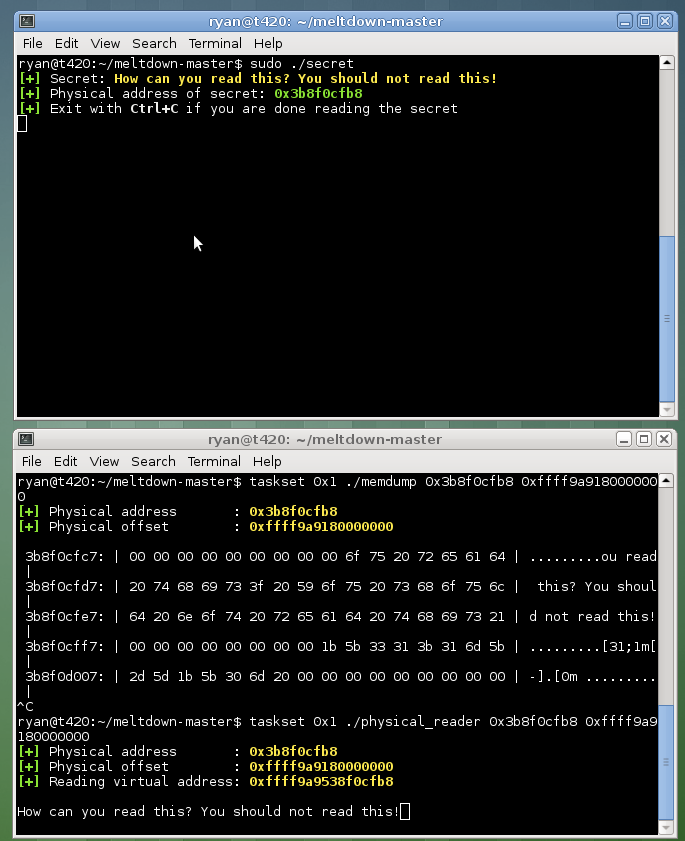
The third demo tested how reliably the physical memory can be read. Running this test, Thoryk was able to determine a 99.93% success rate. The fourth demo attempted to directly read the physical memory. For the purpose of the demo, a human-readable string of data was placed into memory, which Thoryk then confirmed he was able to read, as well as the address and offset of the physical map. The final demo dumped the contents of the physical memory in a hexdump-like format.
Having explored the particulars of the Meltdown exploit with his proof-of-concept, Ryan recommends that users avoid using any computer susceptible to the Meltdown bug as a multi-user system.
All demos can be found online at https://github.com/IAIK/meltdown.
Videos of the demos are available and include:
Video #1 shows how Meltdown can be used to spy in realtime on a password input.
Video #2 shows how Meltdown leaks physical memory content.
Video #3 shows how Meltdown reconstructs a photo from memory.
Video #4 shows how Meltdown reconstructs a photo from memory which is encoded with the FLIF file format.
Video #5 shows how Meltdown leaks uncached memory.